Lockheed Martin Killchain
Author: Roger C.B. Johnsen
Introduction
Lockheed Martin’s Cyber Kill Chain is a security framework designed to help organizations understand and counteract cyber threats. The model outlines the stages of a cyberattack, from initial reconnaissance to the final objective. By identifying and interrupting these stages, organizations can improve their threat detection and response capabilities.
About Model
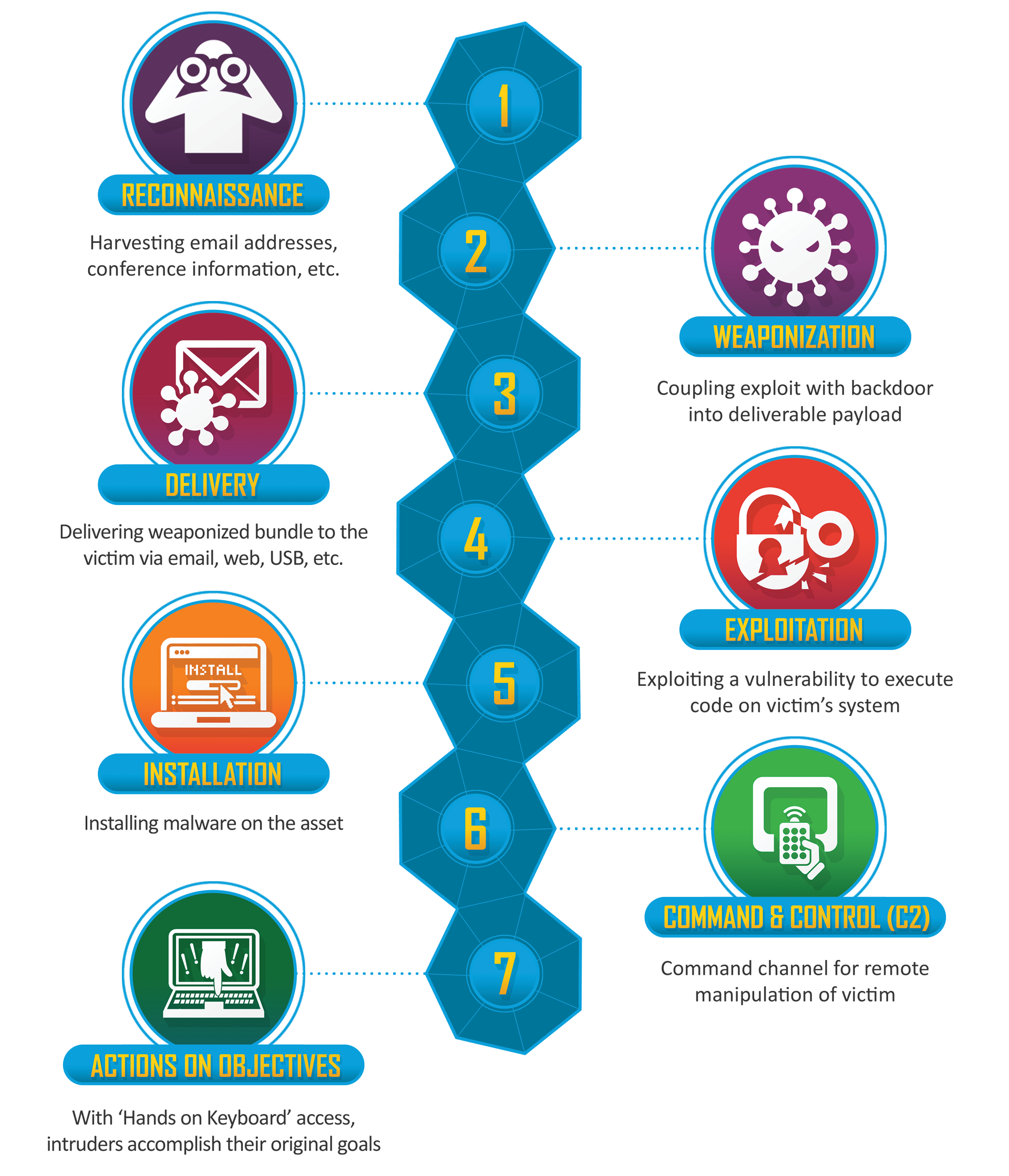
The Cyber Kill Chain consists of seven stages:
- Reconnaissance: Attackers gather information about the target.
- Weaponization: Attackers create a deliverable payload.
- Delivery: The payload is transmitted to the target.
- Exploitation: The payload is executed on the target system.
- Installation: Malware or backdoors are installed.
- Command and Control (C2): Attackers establish communication with the compromised system.
- Actions on Objectives: Attackers achieve their goals, such as data exfiltration or system damage.
This is the official depiction of the model from Lockheed Martin :
Example
Consider a hypothetical scenario where a financial institution is targeted by a cyberattack. Using the Cyber Kill Chain model, the institution’s security team can map out the attack as follows:
- Reconnaissance: Attackers scan the institution’s public-facing websites and social media for vulnerabilities.
- Weaponization: They craft a phishing email containing a malicious PDF.
- Delivery: The phishing email is sent to an employee.
- Exploitation: The employee opens the PDF, triggering a vulnerability in the PDF reader.
- Installation: A remote access Trojan (RAT) is installed on the employee’s computer.
- Command and Control: The RAT connects back to the attacker’s server.
- Actions on Objectives: Attackers move laterally through the network to access sensitive financial data.
Practical Application
In threat hunting, the Cyber Kill Chain can be used to proactively search for indicators of compromise (IOCs) and anomalous activities within each stage of the attack process. Here’s how:
Reconnaissance:
- Monitor for unusual scanning activities and attempts to access public information.
- Use threat intelligence feeds to identify potential attacker IP addresses.
Weaponization:
- Analyze email attachments and web downloads for malware signatures.
- Use sandbox environments to detonate suspicious files.
Delivery:
- Implement email filtering and web gateway protections to block malicious content.
- Educate employees on phishing tactics to reduce successful delivery rates.
Exploitation:
- Patch vulnerabilities promptly to prevent exploitation.
- Use endpoint detection and response (EDR) tools to identify exploitation attempts.
Installation:
- Monitor for changes in system files and registry entries.
- Use application whitelisting to prevent unauthorized software installations.
Command and Control:
- Monitor network traffic for unusual outbound connections.
- Use intrusion detection systems (IDS) to identify known C2 patterns.
Actions on Objectives:
- Monitor for unusual data access and exfiltration activities.
- Implement data loss prevention (DLP) solutions to protect sensitive information.
Resources
Books:
- “The Cyber Kill Chain: Threat Hunting Across the Attack Lifecycle” by Steven Stasiukonis
- “The Hacker Playbook 3: Practical Guide To Penetration Testing” by Peter Kim
Websites:
Tools:
- Threat intelligence platforms (e.g., ThreatConnect, Recorded Future)
- EDR solutions (e.g., CrowdStrike Falcon, Carbon Black)
- Network monitoring tools (e.g., Wireshark, Zeek)
By leveraging the Cyber Kill Chain model, organizations can enhance their threat hunting processes, improve their security posture, and effectively mitigate cyber threats.
Revision
| Revised Date | Comment |
|---|---|
| 06.10.2024 | Improved formatting and wording |