Pyramid of Pain
Author: Roger C.B. Johnsen
Introduction
The Pyramid of Pain is a conceptual model created by David J. Bianco that illustrates the relative difficulty and impact of detecting and responding to different types of indicators used in threat hunting and incident response. The model helps cybersecurity professionals understand the value of various types of indicators and how effectively they can disrupt adversary activities.
About Model
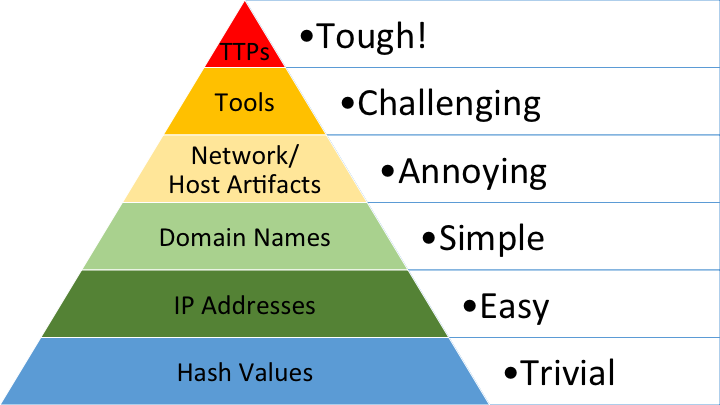
The Pyramid of Pain consists of six levels:
Each level representing a type of indicator and the associated pain (difficulty) it causes to the adversary when detected and mitigated:
- Hash Values: Specific file hashes (e.g., MD5, SHA-1).
- IP Addresses: Specific IP addresses used by adversaries.
- Domain Names: Specific domain names used by adversaries.
- Network/Host Artifacts: Specific characteristics of network traffic or host-based artifacts.
- Tools: Specific tools used by adversaries.
- Tactics, Techniques, and Procedures (TTPs): The adversary’s methods and strategies.
The higher the indicator on the pyramid, the more pain it causes the adversary when detected and mitigated, as it forces them to change their tactics, tools, or procedures, which is more challenging and time-consuming than merely changing a hash or IP address.
Example
Consider a scenario where a company detects a cyberattack using the Pyramid of Pain:
- Hash Values: The company identifies and blocks a known malicious file by its hash.
- IP Addresses: The attacker’s command and control (C2) server IP address is detected and blocked.
- Domain Names: The domain name used for phishing emails is identified and blocked.
- Network/Host Artifacts: Unusual patterns in network traffic are detected, such as specific HTTP headers used by malware.
- Tools: The attacker is using the Mimikatz tool for credential dumping, which is detected and blocked.
- TTPs: The attacker uses specific techniques for lateral movement (e.g., Pass-the-Hash), which are identified and mitigated by enhancing detection and response strategies.
Practical Application
In threat hunting, the Pyramid of Pain can be used to prioritize detection and response efforts based on the impact on the adversary:
Hash Values:
- Detection: Use file integrity monitoring and antivirus software to detect malicious hashes.
- Response: Block detected hashes and share them with threat intelligence communities.
IP Addresses:
- Detection: Monitor network traffic for connections to known malicious IP addresses.
- Response: Block detected IP addresses at the firewall and update network blacklists.
Domain Names:
- Detection: Use DNS filtering and threat intelligence feeds to identify malicious domains.
- Response: Block detected domains and update DNS blacklists.
Network/Host Artifacts:
- Detection: Analyze network traffic and host logs for unusual patterns or artifacts.
- Response: Implement detection rules and alerts for identified artifacts.
Tools:
- Detection: Monitor for known tools and their signatures (e.g., Mimikatz).
- Response: Block execution of detected tools and enhance endpoint security measures.
TTPs:
- Detection: Use the MITRE ATT&CK framework to identify and detect adversary techniques.
- Response: Develop and implement detection and mitigation strategies for identified TTPs.
Example Scenario
Suppose an organization detects an ongoing attack. By leveraging the Pyramid of Pain, they can disrupt the adversary at various levels:
- Hash Values: They detect a malicious file hash and block it.
- IP Addresses: They identify the C2 server’s IP address and block it.
- Domain Names: They block the phishing domain used by the attacker.
- Network/Host Artifacts: They detect unusual network traffic patterns indicative of the attack and alert the security team.
- Tools: They identify and block the use of Mimikatz by monitoring for its signatures.
- TTPs: They enhance their detection and response capabilities to mitigate lateral movement techniques used by the attacker.
Resources
Books:
- “The Threat Hunter Playbook: A Practical Guide to Hunt and Detect Advanced Threats” by J. H. Rose
- “Threat Hunting with the MITRE ATT&CK Framework” by Bhushan Lakhe
Websites:
Tools:
- Threat intelligence platforms (e.g., ThreatConnect, Recorded Future)
- Endpoint detection and response (EDR) solutions (e.g., CrowdStrike Falcon, Carbon Black)
- Network monitoring and analysis tools (e.g., Wireshark, Zeek)
By applying the Pyramid of Pain model in threat hunting, organizations can prioritize their efforts to cause maximum disruption to adversaries, making it more challenging and costly for them to achieve their objectives.
Revision
| Revised Date | Comment |
|---|---|
| 06.10.2024 | Improved formatting and wording |